Question & Answer
Question
Answer
ClearQuest Web supports HTTP Strict Transport Security (HSTS) header. For more information, see Setting up HTTP Strict Transport Security (HSTS).
ClearQuest Web supports X-Content-Type-Options header. For more information, see technote How to set X-Content-Type-Options HTTP header.
ClearQuest Web supports X-XSS-Protection header. For more information, see X-XSS-Protection.
Content-Security-Policy (CSP) header is not required by ClearQuest Web. CSP header is used to protect from Cross-Site Scripting (XSS) and Cross-Frame Scripting (XFS). There are many XSS and XFS protections in ClearQuest Web as HTTPOnly attribute and escaping for XSS, and X-Frame-Options header for XFS.
ClearQuest Web utilizes escaping and supports HTTPOnly to protect from XSS. For more information, see technote Setting the SECURE and HTTPOnly attributes on the cookie for Rational ClearQuest Web server.
ClearQuest Web supports the secure attribute. For more information, see technote Setting the SECURE and HTTPOnly attributes on the cookie for Rational ClearQuest Web server.
ClearQuest Web utilizes X-Frame-Options header to protect from XFS. For some known iframes like the welcome page, ClearQuest Web will check that the referrer (parent frame's domain) is authorized, wherein additional X-Frame-Options header for these requests is not needed.
ClearQuest Web utilizes the CSRF token (cquid) to protect from CSRF. dojo.preventCache in the URL requests is not a session or cookie. It's just a random argument added to the URL to prevent the browser from caching it.
ClearQuest supports the brute force protection. For more information, see technote How to protect your ClearQuest deployment from brute-force password attacks.
To mitigate weak password policy, you must implement a combination of all three source protection such as LDAP, SSO and brute force protection.
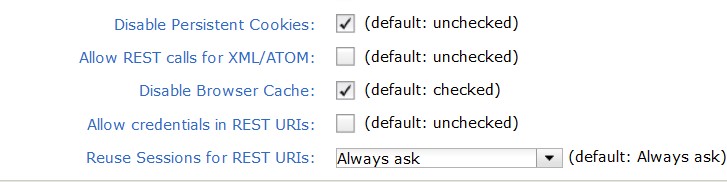
To disable persistent cookies is supported by ClearQuest Web. There is a security option 'Disable Persistent Cookies' in the ClearQuest Web Site Configuration dialog. The option can be checked to not store persistent cookies on the client computers.
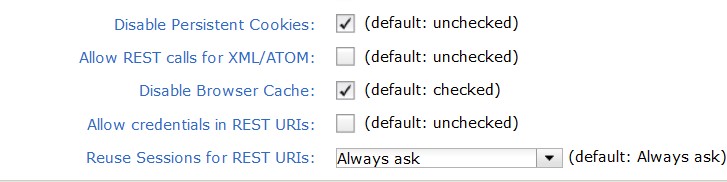
To disable the browser cache is supported by ClearQuest Web. There is a security option 'Disable Browser Cache' in the ClearQuest Web Site Configuration dialog. The option is checked by default.
See below how to enable TLS 1.2 only and disable other TLS protocols in the IBM HTTP Server (IHS).
Add the following lines in the VirtualHost snippet for your SSL configuration in the IHS httpd.conf file:
SSLProtocolEnable TLSv12
SSLProtocolDisable SSLv2 SSLv3 TLSv10 TLSv11
If you want to allow only a specific Cipher within TLS 1.2 (example below), add SSLCIpherSpec directive as a 3rd line:
SSLCipherSpec TLSv12 TLS_RSA_WITH_AES_256_CBC_SHA256
ClearQuest supports secure ciphers. For more information, see technote Configuring IBM Rational ClearQuest with LDAP user authentication for TLS 1.2 to support NIST SP 800-131A guidelines.
Feature-Policy and Permissions-Policy headers are not required by ClearQuest Web. Feature-Policy has been deprecated and is superseded by Permissions-Policy.
ClearQuest does not need to explicitly enable access to things that are disabled by default. ClearQuest does not have support for plugins. ClearQuest does not require access to any feature that may have security issues (GPS, Camera, microphone, etc.).See the examples below of the Feature-Policy or Permission-Policy headers that could possibly be used in IBM HTTP Server (IHS) httpd.conf so that they would stop getting flagged:
Header set Feature-Policy "accelerometer 'none'; camera 'none'; geolocation 'none'; gyroscope 'none'; magnetometer 'none'; microphone 'none'; payment 'none'; usb 'none'"Header set Permissions-Policy "accelerometer=(), camera=(), geolocation=(), gyroscope=(), magnetometer=(), microphone=(), payment=(), usb=()"
Referrer-Policy header is not required by ClearQuest Web. ClearQuest does not rely on sending referral information to any outside source.
See some examples below of the Referrer-Policy header that could possibly be used in IBM HTTP Server (IHS) httpd.conf so that it would stop getting flagged:Header set Referrer-Policy "no-referrer"
Referrer-Policy: strict-origin-when-cross-origin as the default referrer policy, which is more secure than the current default which is usually "no-referrer-when-downgrade".ClearQuest administrators can either upgrade to WebSphere Application Server (WAS) 9 or disable X-Powered-By header.
The Servlet API is provided by WAS. WAS 9.0 and above supports Servlet 3.1. For more information, see Java Servlet considerations.
For how to disable X-Powered-By header, see Disable X-Powered-By Header.
Was this topic helpful?
Document Information
Modified date:
17 November 2021
UID
ibm16515616